Barracuda Study Uncovers Scammers Targeting Work Email Accounts for Financial Gain
Barracuda, a cybersecurity company, has revealed a troubling pattern in a new study. It highlights how email scammers are resorting to multiple Bitcoin wallets to extort money from their targets. These fraudsters employ various strategies, such as threatening to expose compromising or illegal content, targeting multiple work email accounts simultaneously, and demanding modest payments of approximately $1,000 USD in Bitcoin. By adopting this method, attackers can evade detection and prevent arousing suspicion among potential victims, security teams, and payment systems.
Insights from Columbia University research
Barracuda’s findings are based on an analysis by a team of researchers at Columbia University, who examined 300,000 emails marked as extortion scams over a 12-month period. The primary goal was to gain an understanding of the financial infrastructure used by phishing email criminals.
Extortion attacks typically involve threats to reveal compromising personal information, such as specific photos, videos, or information about illegal online activity, with the intent of forcing victims to make payments, often in cryptocurrencies such as Bitcoin. The research findings are outlined in a comprehensive report called Barracuda Threat Spotlight.
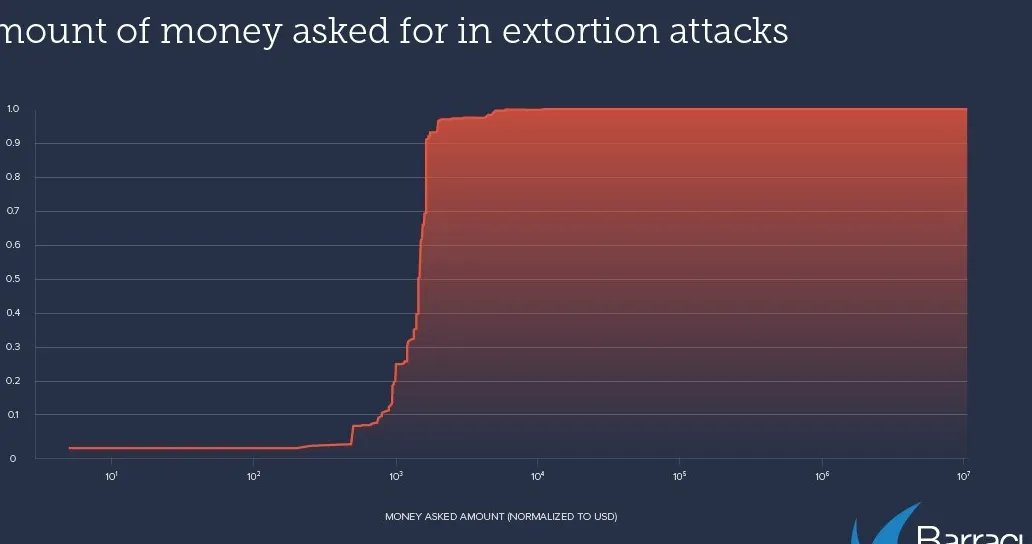
Centralized wallet usage and attack patterns
The detection data provided valuable insights into the attack pattern. Specifically, the analysis revealed that the attackers used a staggering 3,000 unique Bitcoin wallet addresses. However, it was found that only 100 wallets were responsible for 80% of the ransomware emails. This highlights the fact that a relatively small number of attackers were behind most of these malicious campaigns.
Additionally, the researchers found that 97% of the sender accounts associated with the ransomware sent fewer than 10 attack emails. Additionally, 90% of the attacks demanded payments of less than $2,000 in Bitcoin.
Asaf Cidon, assistant professor of electrical engineering at Columbia University, stated: “Our analysis suggests that extortion scams are carried out by a relatively small number of actors, each of whom launches multiple small-scale attacks with reasonable extortion demands. These relatively modest amounts make it more likely that targets will cooperate with the extortion, and the relatively small number of emails per sender making it easier for attackers to evade detection by traditional security techniques and payment service providers’ anti-fraud measures and to avoid attracting the attention of law enforcement and the media. which alerts potential victims to the scam.”
The importance of preventing extortion attacks
Nishant Taneja, Director of Product Marketing for Email Protection at Barracuda, emphasized the importance of taking ransomware attacks seriously, especially when they target individuals through work email accounts. Taneja emphasized the need for security teams to investigate how the attackers gained access to the account information and whether it had been compromised or stolen at some point. Such scenarios have significant security implications for both the target person and the company they work for. The confusion and anxiety caused by these attacks often makes victims more likely to give in to extortion demands.
To protect employees and organizations from phishing scams, security teams should consider investing in AI-based email security solutions that can detect and block such malicious emails before they reach the intended recipient. In addition, companies should prioritize employee training and implement security policies that prevent staff from using work email accounts to access third-party sites or store sensitive personal information on work devices.




